Welcome to the official website of goalkeeper technology group.
Welcome to the official website of goalkeeper technology group.

When you are still talking about the paragraph, something has been achieved.
The word "unlocked with your heart" will be seen in the section on the face payment. More often, I will see it in the chicken soup. "When there are obstacles in your love path, you have to learn to unlock it with your heart."
However, you probably haven't thought about it. What you can unlock with your heart is not just a relationship, but a laptop.
Yes, you can do this.
The original intention of the researcher: privacy is too easy to be leaked
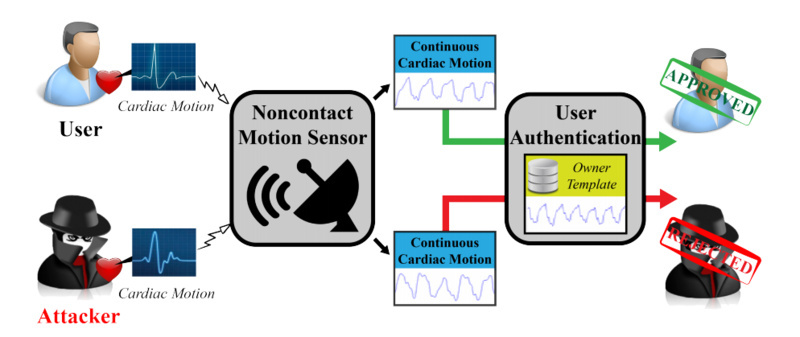
Researchers at the University of Buffalo (UB) have invented a computer authentication system that can log in using the shape and size of your heart. It uses a low level of Doppler radar to continuously scan the size of your heart, as long as you are in the right position, it will allow you to enter.
In this case, when you go out for coffee, you don't worry about who your computer will steal passwords and steal information.
This is the use of Busheng Xiaomin as my own. Looking at the world, it will have some different meanings.
The demand for safer certification methods by governments and private companies is growing. More and more events make us feel uneasy. From the data leak of Yahoo's 1 billion account, to the recent leak of 143 million accounts of Equifax, the US credit bureau, every time it is shocking.
Specific to the individual, whether it is weak encryption, or carelessness, often give hackers a chance. In 2014 alone, more than one billion people’s personal files were hacked, including health, finance, e-mail, home addresses, social accounts and other personal information.

The principal author of the study, Wenyao Xu, an assistant professor in the Department of Computer Science and Engineering at the University of Buffalo, did not hide his ambition: "We want to use it on every computer because everyone needs privacy."
Currently, various authentication solutions have certain limitations.
Specifically, traditional methods require users to participate in an authentication system, such as scanning fingerprints or entering passwords. These methods are risky in practice regardless of the strength of the "password".
Some studies have also proposed advanced verification mechanisms based on user behavior, such as keystroke mechanics and gaze mode. Keystroke mechanics require the user to continue typing on the keyboard, while the gaze mode requires the user to constantly look at the screen. Think about this picture, is it a bit of a second?
Other methods, such as facial recognition, have also been reported to be easily scammed by cameras.
Recently, other biometrics have also emerged. For example, the brush payment we reported a few days ago used finger vein recognition technology. However, this technique requires close contact with the human body.
Heart scans are completely unnecessary, and the researchers say that a distance of 30 meters can identify a person.
What kind of existence is this?
Let's take a closer look, what kind of existence is this?
Simply put, it is the way to authenticate your heart as an identifier. The system uses a low level of Doppler radar to measure your heart and then continuously monitor your heart to ensure that no one else is involved to run your computer.
This system takes 8 seconds to scan the heart, after which the monitor can continue to recognize the heart.
The researchers wrote in the paper: "We conducted a trial with 78 subjects to assess heart scan accuracy, certification time, persistence, usability in a complex environment, and vulnerability. Everyone has four heart cycles (From the beginning of a heartbeat to the beginning of the next heartbeat) for identification. The results show that the success rate of heart scan is 98.61% and the error rate is 4.42%."
These data show that this is a promising identity authentication system.
Moreover, as mentioned above, it can work at a great distance.
The team even envisioned that using the method to verify people outside of 98 feet (30 meters) sounds a little scary, but you will be grateful for this verification method when you are about to miss the opportunity.
After you are an adult, your heart will not change except for extremes such as heart disease. And, only when people are alive, there is heart movement, so don't worry about the gangsters hurting people in order to hijack your information.
In addition, the system has been in use for three years in the production process, and the researchers did not find any two people with the same heart.
However, the next question is, the old man holding the radar to scan the heart, the heart will not receive interference?
In fact, the radar's signal strength is much lower than WiFi, so there is no threat.
Xu said: "We live in a wireless network environment every day. This new system is as safe as those of wifi devices. The power consumption of radar is only about 5 milliwatts, or even less than 1% of smartphone radiation."
As a biometric system, it should have a certain anti-interference ability to the surrounding environment. Based on the camera's verification method, it will be affected by the brightness of the light. If the glare or the light is too weak, it will affect the recognition effect.
In contrast, heart scans use a powerful radio signal that penetrates obstacles to accurately sense heart motion.
In terms of economic costs, this technology has two advantages:
First, some biometric technologies are highly reliable, but in terms of information acquisition, expensive equipment and specific conditions are required, such as the iris/retina authentication system. Cardiac scanning can assemble radar sensors using low-cost off-the-shelf components.
Second, heart scans can be easily integrated with existing one-pass verification techniques such as PIN, fingerprint, iris scanning, facial recognition, etc. to enhance the verification capabilities of existing systems.

Airport security
Xu plans to miniaturize the system and install it on the corner of the computer keyboard. It can also be used for identification of mobile phone users. There is also an airport security check, 30 meters away from the inspection, it sounds quite a good choice.
 Pay attention to our public address.
Pay attention to our public address.
